VPN Logging Policies: What You Need to Know
Your Complete Guide to Understanding No-Log VPNs and Privacy Protection
Table of Contents
Understanding VPN logging policies is crucial for anyone serious about online privacy and security. With increasing concerns about data collection and surveillance, knowing what information your VPN provider collects, stores, and potentially shares has become more important than ever. This comprehensive guide will explain VPN logs, explore no-log VPNs, and help you understand VPN privacy policies to make informed decisions about your digital security.
Throughout this article, we’ll cover the different types of VPN logs, examine statistical data about VPN logging practices, and provide practical advice on choosing truly private VPN services. Whether you’re a privacy-conscious individual or a business professional, understanding these concepts will help you protect your online activities and maintain digital anonymity.
What Are VPN Logs?
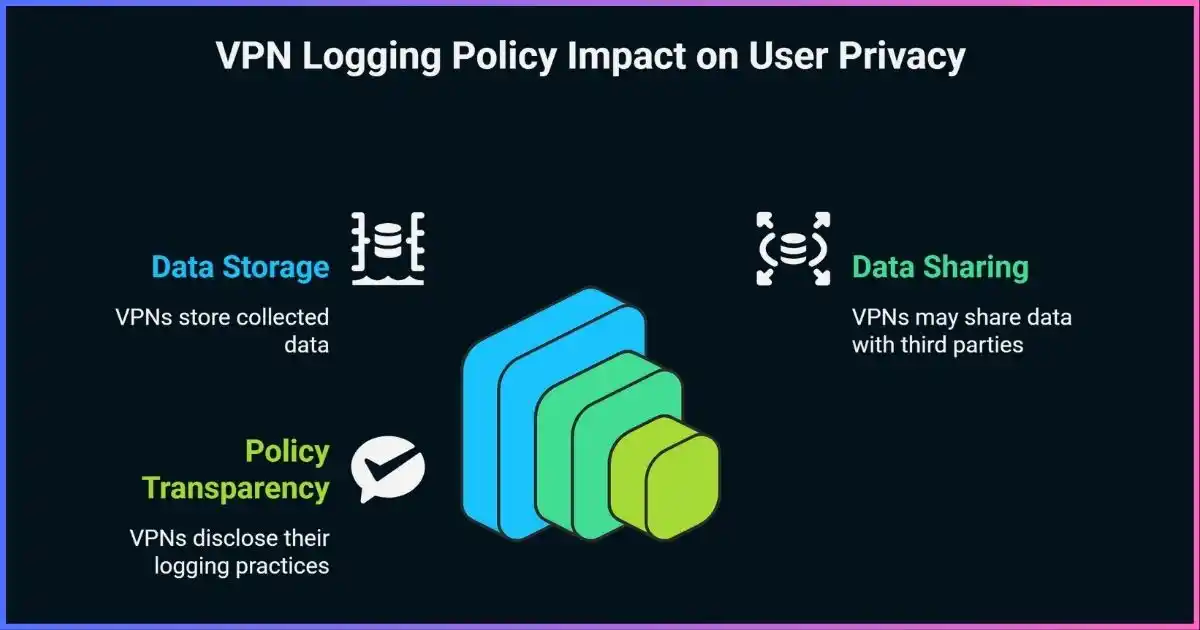
VPN logs are records of user activity and connection data that VPN providers may collect during your browsing sessions. These logs can contain various types of information, from basic connection timestamps to detailed records of websites visited and data transferred. Understanding what constitutes VPN logs is the first step in protecting your privacy.
The practice of logging varies significantly between VPN providers. While some maintain detailed records for operational purposes, others operate under strict no-log policies that prohibit the collection of user activity data. The difference between these approaches can have profound implications for your privacy and security.
VPN logs explained simply: they represent any data that could potentially identify you, your online activities, or your browsing patterns. This information becomes particularly sensitive when it can be linked to your real identity or used to reconstruct your digital footprint.
Types of VPN Logs
VPN providers may collect different categories of logs, each with varying implications for your privacy. Understanding these categories helps you evaluate VPN privacy policies and make informed decisions about which services to trust.
Usage Logs (High Risk)
- • Websites visited
- • Files downloaded
- • Bandwidth usage per session
- • Time spent on specific sites
- • Application usage data
Connection Logs (Medium Risk)
- • Connection timestamps
- • IP addresses
- • Server locations used
- • Session duration
- • Data transferred amounts
Minimal Logs (Lower Risk)
Some VPN providers collect minimal operational data that doesn’t compromise privacy:
- • Aggregated bandwidth statistics
- • Server performance metrics
- • Anonymous usage patterns
- • Technical diagnostic information
The key distinction lies in whether the collected data can be linked to individual users. True no-log VPNs avoid collecting any information that could identify users or their activities, while others may collect anonymized data for service improvement purposes.
Understanding No-Log VPNs
No-log VPNs represent the gold standard for privacy protection in the VPN industry. These services commit to not collecting, storing, or sharing any information that could identify users or their online activities. However, the term “no-log” can be interpreted differently by various providers, making it essential to understand what true no-log policies entail.
A genuine no-log VPN policy means the provider cannot produce user activity records even if compelled by legal authorities. This protection extends beyond simple privacy preferences to fundamental digital rights and freedom from surveillance. The most reputable no-log VPNs undergo independent security audits to verify their claims and demonstrate their commitment to user privacy.
What True No-Log VPNs Don’t Collect
- • Browsing history
- • Traffic destinations
- • Data content
- • DNS queries
- • Connection timestamps
- • IP addresses
- • Session information
- • Bandwidth usage
VPN Logging Statistics and Industry Data
Recent studies reveal concerning trends in VPN logging practices across the industry. Understanding these statistics helps consumers make informed decisions about VPN providers and highlights the importance of choosing truly private services.
VPN Provider Logging Practices ()
User Privacy Concerns When Choosing VPNs
| Statistic | Percentage | Source |
|---|---|---|
| VPN users concerned about logging | 78% | Privacy Research Institute |
| VPN providers with verified no-log policies | 31% | VPN Security Study |
| Users who read privacy policies | 23% | Digital Privacy Survey |
| VPN providers that underwent security audits | 18% | Cybersecurity Audit Report |
These statistics reveal a significant gap between user expectations and industry practices. While the majority of VPN users express concerns about logging, only a minority of providers have undergone independent verification of their no-log claims. This underscores the importance of choosing VPN services with proven track records and transparent privacy policies.
Reading VPN Privacy Policies
VPN privacy policies serve as legal documents that outline how providers collect, use, and protect user data. However, these policies can be complex and filled with legal jargon that obscures important details. Learning to read and understand these policies is essential for making informed decisions about your digital privacy.
Key Elements to Look For
Data Collection Practices
- • What data is collected
- • How long data is stored
- • Data sharing policies
- • Third-party integrations
Legal Compliance
- • Jurisdiction and laws
- • Government request policies
- • Transparency reporting
- • User notification procedures
When evaluating VPN privacy policies, pay special attention to vague language or broad exceptions that could undermine no-log claims. Phrases like “may collect,” “under certain circumstances,” or “when required by law” often indicate potential logging practices that contradict advertised privacy protections.
Red Flags in Privacy Policies
- • Vague definitions of “personal information”
- • Broad data sharing permissions
- • Undefined data retention periods
- • Extensive third-party partnerships
- • Lack of transparency about government requests
- • Frequent policy changes without notification
The best VPN privacy policies are clear, specific, and regularly updated to reflect current practices. They should explicitly state what data is not collected and provide transparent procedures for handling any exceptional circumstances. Look for providers that publish transparency reports and undergo regular independent audits to verify their privacy claims.
How to Choose a No-Log VPN
Selecting a truly private VPN requires careful evaluation of multiple factors beyond marketing claims. The most important consideration is verifying that the provider’s no-log policy is genuine and has been independently validated through security audits or legal challenges.
Security Audits
Independent security audits verify no-log claims and identify potential vulnerabilities in VPN infrastructure.
Legal Jurisdiction
VPN providers based in privacy-friendly jurisdictions face fewer legal pressures to maintain user logs.
Transparency Reports
Regular transparency reports demonstrate commitment to user privacy and accountability.
Essential Evaluation Criteria
Independent Security Audits
Look for providers that regularly undergo third-party security audits by reputable cybersecurity firms.
Open Source Software
Open source VPN applications allow independent verification of security claims and code integrity.
RAM-Only Servers
Diskless servers that store no data permanently provide additional protection against data retention.
Legal Test Cases
Providers that have successfully defended their no-log policies in court demonstrate genuine commitment to privacy.
Legal Considerations and Jurisdictions
The legal environment surrounding VPN operations varies significantly across different jurisdictions, directly impacting how providers can implement and maintain no-log policies. Understanding these legal frameworks helps explain why some VPN services can offer stronger privacy protections than others.
Privacy-Friendly Jurisdictions
Countries with strong privacy laws and limited data retention requirements provide the best environment for true no-log VPN operations. These jurisdictions typically have constitutional protections for privacy, limited government surveillance powers, and strong legal frameworks that protect user data from unauthorized access.
Data Retention Laws Impact
Some countries require internet service providers to retain user data for extended periods:
- • European Union: Up to 2 years for telecommunications data
- • United States: No federal requirement, but individual states may vary
- • Australia: 2 years for telecommunications metadata
- • Russia: 6 months for internet traffic data
- • Switzerland: No mandatory data retention for VPN providers
VPN providers must navigate complex legal landscapes that can change rapidly. The most privacy-conscious services often establish their operations in jurisdictions with the strongest privacy protections and maintain transparent policies about how they respond to legal requests for user information.
Related: Top Reasons to Mask Your IP Address
Related: How to Set Up a Proxy Server on Windows & Mac
Frequently Asked Questions
A no-log VPN policy means the provider does not collect, store, or monitor any information about your online activities, connection times, IP addresses, or browsing history. This ensures that even if the VPN company is compelled by legal authorities to provide user information, they have no data to share.
Look for independent security audits, transparency reports, and court cases where the VPN provider successfully demonstrated they had no user data to provide. Reputable providers often publish audit results and maintain open-source software that can be independently verified.
Most free VPN services are not true no-log providers. They often collect user data to generate revenue through advertising or data sales. Free services typically have less stringent privacy policies and may log extensive user information to support their business model.
Connection logs record when you connect to the VPN, your IP address, and session duration. Usage logs track what you do online, including websites visited and files downloaded. True no-log VPNs collect neither type of information, while some providers may collect minimal connection data for technical purposes.
Unfortunately, yes. Some providers use misleading marketing claims about no-log policies while still collecting certain types of data. This is why independent audits and transparency reports are crucial for verifying actual practices beyond marketing statements.
No-log VPN providers use technical solutions like RAM-only servers that don’t store data permanently, automated systems that require no manual intervention, and architectural designs that prevent data collection. They focus on providing secure connections without maintaining records of user activities.
Yes, significantly. Countries with strong privacy laws and limited surveillance powers provide better environments for no-log operations. VPN providers in countries with mandatory data retention laws may be legally required to maintain certain types of logs, regardless of their privacy preferences.
Ready to Protect Your Privacy?
Choose a VPN service with a proven no-log policy and independent security audits.
Start Your Surfshark VPN Journey TodayDisclosure: We may earn commission for purchases that are made by visitors on this site at no additional cost on your end. All information is for educational purposes and is not intended for financial advice. Read our affiliate disclosure.