What Is a Proxy Server and How Does It Work?
Your Complete Guide to Understanding Proxy Meaning and Implementation
Table of Contents
In today’s digital landscape, understanding what is a proxy and how proxy server works has become crucial for both individuals and businesses. The proxy meaning extends far beyond simple internet intermediation—it encompasses privacy protection, security enhancement, and performance optimization. This comprehensive guide will explore the fundamental concepts of proxy servers, their operational mechanisms, various types, and practical applications that have made them indispensable in modern networking.
Whether you’re a technical professional seeking to implement proxy solutions, a business owner exploring privacy options, or simply curious about how proxy servers function, this article provides detailed insights into every aspect of proxy technology. We’ll examine market statistics, security considerations, implementation strategies, and answer the most common questions about proxy servers.
Ready to Get Started with Premium Proxy Services?
Experience the power of professional proxy solutions with ProxyShare’s reliable and secure services.
Try ProxyShare NowWhat Is a Proxy Server?
A proxy server is an intermediary server that acts as a gateway between client devices and the internet. When you connect to a proxy server, your internet requests are first sent to the proxy, which then forwards them to the destination server on your behalf. The response from the destination server is then sent back to the proxy, which forwards it to your device.
The proxy meaning in networking terminology refers to this intermediary role—literally standing as a representative or substitute for another entity. In the context of internet communications, the proxy server represents your device when communicating with web servers, effectively masking your direct connection and providing various benefits including privacy, security, and performance enhancements.
Key Characteristics of Proxy Servers:
Intermediary Function
Acts as a middleman between client and server communications
Identity Masking
Hides your real IP address from destination servers
Traffic Filtering
Can filter, monitor, and control internet traffic
Performance Enhancement
Provides caching and load balancing capabilities
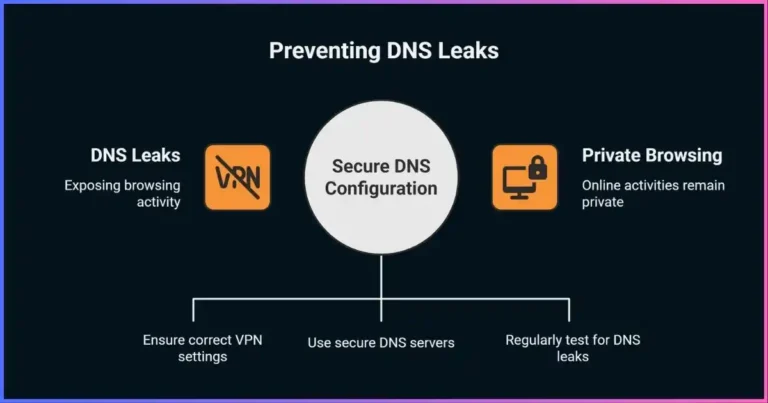
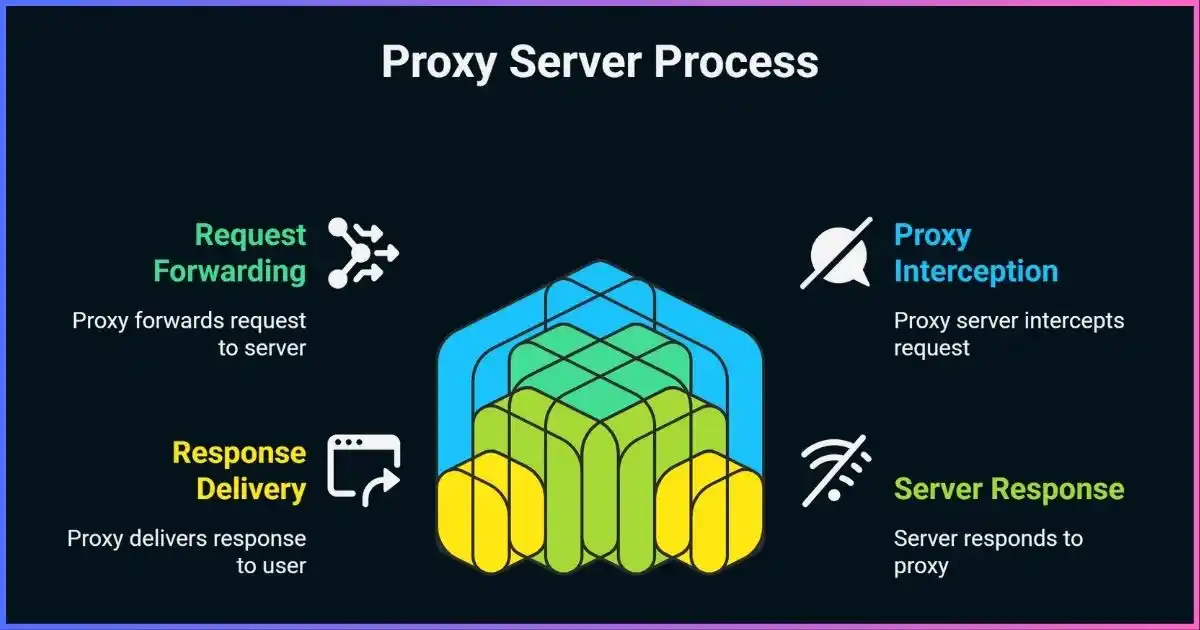
How Proxy Servers Work
Understanding how proxy server works requires examining the step-by-step process of proxy communication. The proxy server operates by intercepting client requests, processing them according to configured rules, and then forwarding them to the intended destination while maintaining the ability to modify, filter, or cache the data flow.
The Proxy Communication Process:
Client Request Initiation
Your device sends a request to the proxy server instead of directly to the destination server
Proxy Processing
The proxy server receives, analyzes, and potentially modifies the request
Request Forwarding
The proxy forwards the request to the destination server using its own IP address
Response Handling
The destination server responds to the proxy server with the requested data
Client Delivery
The proxy server sends the response back to your device
This process allows the proxy server to act as a transparent intermediary while providing additional functionality such as caching frequently requested content, filtering malicious requests, balancing loads across multiple servers, and maintaining logs of all communications for security and monitoring purposes.
Types of Proxy Servers
Proxy servers come in various types, each designed for specific use cases and operational requirements. Understanding these different types is crucial for selecting the appropriate proxy solution for your needs.
HTTP Proxies
HTTP proxies are designed specifically for web traffic and operate at the application layer. They understand HTTP protocols and can interpret web requests, making them ideal for web browsing, content filtering, and caching.
Best for:
- Web browsing and HTTP/HTTPS traffic
- Content filtering and monitoring
- Web scraping applications
- Basic anonymity for web activities
SOCKS Proxies
SOCKS proxies operate at a lower level than HTTP proxies and can handle any type of traffic, including TCP and UDP protocols. They’re more versatile but don’t understand the content they’re transmitting.
Best for:
- All types of internet traffic
- Gaming and P2P applications
- Email and FTP transfers
- Applications requiring protocol flexibility
Residential Proxies
Residential proxies use IP addresses assigned to real residential locations by ISPs. They appear as regular home internet connections, making them less likely to be detected and blocked.
Best for:
- Social media management
- Market research and data collection
- Ad verification and SEO monitoring
- Accessing geo-restricted content
Datacenter Proxies
Datacenter proxies are hosted in data centers and offer high speed and reliability. They’re not associated with residential ISPs but provide excellent performance for high-volume applications.
Best for:
- High-volume data scraping
- Load testing and performance monitoring
- Price monitoring and comparison
- Academic research and data analysis
Need Help Choosing the Right Proxy Type?
ProxyShare offers all types of proxies with expert guidance to help you select the perfect solution for your needs.
Get Expert ConsultationProxy Market Statistics and Trends
The proxy server market has experienced significant growth in recent years, driven by increasing cybersecurity concerns, data privacy regulations, and the growing need for business intelligence. Understanding these market trends provides valuable insights into the adoption and future of proxy technology.
$3.5 Billion
Global proxy server market size in 2024
$8.2 Billion
Projected market size by 2033
10.3%
Annual growth rate (CAGR) from 2026-2033
4.2 Billion
Internet users engaging with proxy services
Proxy Usage by Industry
Key Market Drivers
Security Concerns
Rising cybersecurity threats drive proxy adoption
Privacy Regulations
GDPR and similar laws increase privacy needs
Business Intelligence
Data collection and analysis requirements
Benefits of Using Proxy Servers
Proxy servers offer numerous advantages for both individual users and organizations. These benefits span across privacy, security, performance, and business functionality, making proxies valuable tools in modern digital operations.
Privacy and Anonymity
Proxy servers mask your real IP address, making it difficult for websites and online services to track your location and identity. This privacy protection is crucial for individuals concerned about digital privacy and businesses conducting competitive research.
- IP address masking and location hiding
- Protection from online tracking and profiling
- Anonymous browsing capabilities
- Reduced digital footprint
Security Enhancement
Proxies act as a barrier between your device and the internet, filtering malicious content and protecting against various cyber threats. They can block access to dangerous websites and prevent malware from reaching your system.
- Malware and phishing protection
- Content filtering and access control
- DDoS attack mitigation
- Network security monitoring
Geographic Flexibility
Proxy servers located in different countries allow you to access geo-restricted content and services. This capability is valuable for businesses operating globally and individuals seeking unrestricted internet access.
- Bypass geo-blocking restrictions
- Access region-specific content
- Global market research capabilities
- International SEO and marketing
Performance Optimization
Many proxy servers offer caching capabilities that store frequently accessed content, reducing load times and bandwidth usage. Load balancing features also help distribute traffic efficiently across multiple servers.
- Content caching and faster loading
- Bandwidth optimization
- Load balancing and traffic distribution
- Reduced server load and improved response times
Ready to Experience These Benefits?
Start leveraging the power of professional proxy services with ProxyShare’s comprehensive solutions.
Start Free TrialSecurity Considerations
While proxy servers provide numerous security benefits, they also introduce certain considerations that users must understand. The security of your proxy implementation depends on various factors including the type of proxy, provider reliability, and configuration settings.
Potential Security Risks
Data Interception
Malicious proxy servers can intercept and log your internet traffic, potentially exposing sensitive information.
Man-in-the-Middle Attacks
Compromised proxies can act as intermediaries in attacks, modifying or stealing data in transit.
Malware Distribution
Untrusted proxy servers may inject malicious code or redirect traffic to harmful websites.
Best Security Practices
Choose Reputable Providers
Select established proxy providers with strong security records and transparent policies.
Use HTTPS Connections
Always use encrypted connections when transmitting sensitive data through proxies.
Regular Security Audits
Conduct regular security assessments of your proxy infrastructure and configurations.
Monitor Traffic Patterns
Implement monitoring systems to detect unusual traffic patterns or security breaches.
Cybersecurity Statistics
Implementation Guide
Implementing proxy servers requires careful planning and consideration of your specific needs. This guide covers the essential steps for successful proxy deployment, from initial assessment to ongoing maintenance.
Step 1: Needs Assessment
Begin by identifying your specific requirements and use cases. Consider factors such as the type of traffic you’ll be handling, geographic requirements, performance needs, and security considerations.
Key Questions to Consider:
- What type of traffic will you be proxying?
- Do you need residential or datacenter proxies?
- What geographic locations do you require?
- What are your performance and reliability requirements?
- What security features are essential?
Step 2: Configuration and Setup
Configure your proxy settings according to your specific requirements. This includes setting up authentication, defining access rules, and configuring any additional features such as load balancing or failover mechanisms.
Configuration Checklist:
- Set up authentication credentials
- Configure IP whitelisting if required
- Define traffic routing rules
- Set up monitoring and logging
- Configure backup and failover options
Step 3: Testing and Optimization
Thoroughly test your proxy implementation to ensure it meets your performance and security requirements. Monitor key metrics and optimize configurations based on real-world usage patterns.
Testing Areas:
- Connection speed and latency
- Reliability and uptime
- Security and privacy protection
- Geographic accessibility
- Load handling and scalability
Need Professional Implementation Support?
ProxyShare provides comprehensive implementation support and consultation services to ensure your proxy deployment is successful.
Get Implementation SupportFrequently Asked Questions
What is the difference between a proxy and a VPN?
While both proxies and VPNs act as intermediaries between your device and the internet, they differ in scope and functionality. A proxy server handles specific applications or protocols (like HTTP traffic), while a VPN creates an encrypted tunnel for all internet traffic from your device. VPNs provide more comprehensive security and privacy protection, while proxies are often faster and more suitable for specific tasks like web scraping or accessing geo-restricted content.
Are free proxy servers safe to use?
Free proxy servers pose significant security risks and are generally not recommended for sensitive activities. Many free proxies are operated by malicious actors who can intercept your data, inject malware, or use your connection for illegal activities. They often lack proper security measures, have poor performance, and may log your activities for profit. For reliable and secure proxy services, it’s advisable to use reputable paid providers like ProxyShare.
How do I choose the right proxy type for my needs?
Choosing the right proxy type depends on your specific use case. For web browsing and HTTP traffic, HTTP proxies are suitable. For applications requiring protocol flexibility or handling various types of traffic, SOCKS proxies are better. If you need to appear as a regular residential user, residential proxies are ideal. For high-volume, high-speed applications, datacenter proxies offer better performance. Consider factors like speed requirements, detection resistance, geographic needs, and budget when making your decision.
Can proxy servers slow down my internet connection?
Proxy servers can potentially slow down your internet connection since they add an extra step in the communication process. However, the impact depends on several factors including the proxy server’s location, quality, load, and your original internet speed. High-quality proxy providers like ProxyShare optimize their infrastructure to minimize speed loss. In some cases, proxies can actually improve performance through caching and load balancing features.
Is it legal to use proxy servers?
Using proxy servers is legal in most countries for legitimate purposes such as privacy protection, security enhancement, and business operations. However, the legality depends on how you use them and local laws. Using proxies to commit fraud, access copyrighted content illegally, or violate terms of service of websites may be illegal. Always ensure you’re complying with local laws and the terms of service of websites you access through proxies.
How many proxy servers do I need for my business?
The number of proxy servers you need depends on your specific business requirements, including the volume of traffic, geographic coverage needed, redundancy requirements, and the nature of your applications. For small businesses, a few high-quality proxies may suffice, while large enterprises might require hundreds or thousands of proxies. Consider factors like concurrent connections, data volume, geographic distribution, and failover requirements when determining your proxy needs.
Conclusion
Understanding what is proxy and how proxy server works is essential in today’s digital landscape. The proxy meaning extends far beyond simple traffic intermediation—it encompasses privacy protection, security enhancement, performance optimization, and business intelligence capabilities that are increasingly vital for both individuals and organizations.
As we’ve explored throughout this comprehensive guide, proxy servers offer numerous benefits including anonymity, security, geographic flexibility, and performance optimization. The growing proxy market, projected to reach $8.2 billion by 2033, reflects the increasing recognition of these benefits across various industries.
Whether you’re implementing proxies for personal privacy, business intelligence, web scraping, or security purposes, selecting the right proxy type and provider is crucial for success. Consider factors such as your specific use case, performance requirements, security needs, and budget when making your decision.
Ready to Get Started with Professional Proxy Services?
ProxyShare offers comprehensive proxy solutions with expert support, reliable infrastructure, and competitive pricing. Whether you need residential proxies, datacenter proxies, or specialized solutions, we have the expertise to help you succeed.
Key Takeaways
- Proxy servers act as intermediaries between clients and servers, providing privacy, security, and performance benefits
- Different proxy types (HTTP, SOCKS, residential, datacenter) serve different purposes and use cases
- The proxy market is experiencing significant growth, driven by security concerns and business intelligence needs
- Security considerations are crucial when implementing proxy solutions
- Proper implementation requires careful planning, testing, and ongoing optimization
Disclosure: We may earn commission for purchases that are made by visitors on this site at no additional cost on your end. All information is for educational purposes and is not intended for financial advice. Read our affiliate disclosure.