VPN Obfuscation: Ultimate Guide
Master the art of hiding your VPN traffic from censors and surveillance
In an increasingly censored digital world, VPN obfuscation has become the ultimate weapon for internet freedom. This comprehensive guide reveals how VPN obfuscation works, why it’s essential for bypassing government censorship and deep packet inspection, and which protocols offer the best protection against sophisticated surveillance systems.
Whether you’re facing the Great Firewall of China, navigating internet restrictions in Iran or Russia, or simply want to protect your privacy from ISP monitoring, understanding VPN obfuscation is crucial. We’ll explore the latest statistics, compare different obfuscation techniques, and show you exactly how to implement these powerful tools for maximum anonymity.
Key Takeaway: VPN obfuscation disguises your VPN traffic as regular internet activity, making it virtually impossible for censors to detect and block your connection.
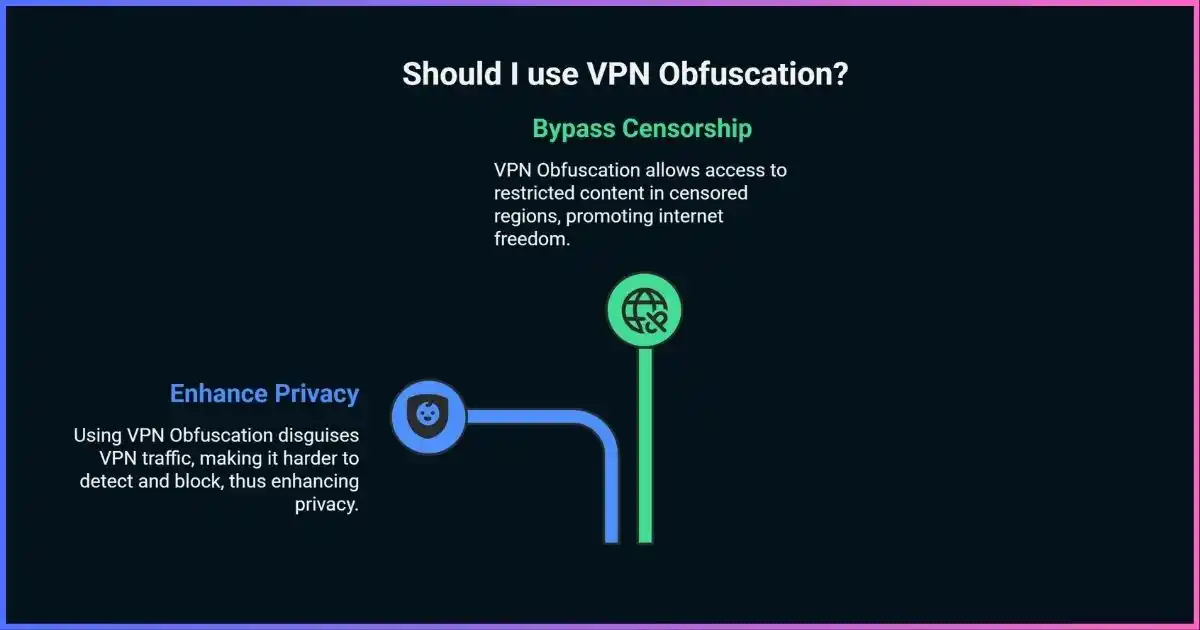
What is VPN Obfuscation?
VPN obfuscation is an advanced technique that transforms your VPN traffic to appear as regular HTTPS web traffic, making it undetectable to deep packet inspection systems and government censors. Unlike standard VPN connections that can be easily identified through their distinctive packet signatures, obfuscated VPN traffic blends seamlessly with normal internet activity.
The technology works by wrapping your encrypted VPN data in additional layers of disguise, effectively creating a “stealth mode” for your connection. This process involves modifying packet headers, altering timing patterns, and sometimes routing traffic through multiple proxy layers to completely mask the VPN’s digital fingerprint.
Global Internet Censorship Statistics
The need for VPN obfuscation has never been more critical. Recent data reveals alarming trends in global internet censorship that directly impact millions of users worldwide.
China’s Internet Restrictions
VPN usage nearly doubled in 2024, with over 30% of internet users affected by the Great Firewall crackdown
Russia’s VPN Surge
VPN demand increased by 2,500% between February and March 2022 following website bans
How VPN Obfuscation Works: Technical Deep Dive
Understanding the technical mechanisms behind VPN obfuscation helps you choose the right solution for your needs. The process involves several sophisticated techniques that work together to create an impenetrable disguise for your VPN traffic.
Deep Packet Inspection (DPI) Evasion
Modern censorship systems use DPI to analyze data packets in real-time, looking for VPN signatures. Obfuscation counters this by:
- Modifying packet headers to mimic HTTPS traffic
- Randomizing packet timing and size patterns
- Implementing traffic shaping to match normal web browsing
- Using domain fronting to hide the true destination
Traffic Disguise
VPN data appears as regular HTTPS traffic
Pattern Randomization
Packet patterns become unpredictable
Multi-Layer Protection
Multiple obfuscation techniques combined
VPN Obfuscation Protocols Comparison
Different obfuscation protocols offer varying levels of security, speed, and effectiveness. Here’s a comprehensive comparison of the most popular techniques used by VPN providers today.
| Protocol | Effectiveness | Speed Impact | Complexity | Use Cases |
|---|---|---|---|---|
| Shadowsocks | High | Minimal | Medium | China, Iran, Russia |
| XOR Scramble | Medium | Low | Low | Basic censorship |
| obfs4 | Very High | Moderate | High | Advanced censorship |
| Stunnel | High | Moderate | Medium | Corporate networks |
| V2Ray/VMess | High | High | Very High | Technical users |
Protocol Effectiveness Analysis
Recent research from academic institutions provides concrete data on how different obfuscation protocols perform against modern detection systems. The following analysis is based on real-world testing against various censorship technologies.
Research Findings
Studies show that OpenVPN flows can be identified in 39 out of 40 vanilla configurations and 34 out of 41 obfuscated configurations, highlighting the importance of choosing the right obfuscation method.
Best Practices for VPN Obfuscation Implementation
Implementing VPN obfuscation effectively requires understanding both the technical aspects and practical considerations. These best practices will help you achieve maximum anonymity while maintaining usable connection speeds.
Configuration Tips
- Use TCP port 443 for maximum stealth
- Enable DNS leak protection
- Choose servers in nearby countries
- Test multiple protocols regularly
Common Mistakes to Avoid
- Using the same server repeatedly
- Ignoring kill switch settings
- Mixing obfuscated and regular traffic
- Neglecting firmware updates
Common Challenges and Solutions
Even with the best obfuscation technology, users may encounter challenges. Understanding these common issues and their solutions can help you maintain a reliable connection in restrictive environments.
Challenge: Slow Connection Speeds
Obfuscation adds processing overhead that can reduce speeds by 10-30%.
Solution: Use lightweight protocols like Shadowsocks or choose servers with dedicated obfuscation hardware.
Challenge: Intermittent Disconnections
Censorship systems constantly evolve, causing previously working connections to fail.
Solution: Enable auto-reconnect features and maintain multiple backup protocols.
Challenge: Mobile Device Compatibility
Some obfuscation protocols have limited mobile support.
Solution: Choose VPN providers with native mobile apps that include obfuscation features.
Future of VPN Obfuscation Technology
As censorship technology becomes more sophisticated, VPN obfuscation must evolve to stay ahead. Emerging trends in this space include machine learning-based traffic analysis and quantum-resistant encryption methods.
Emerging Technologies
AI-Powered Obfuscation
Machine learning algorithms that adapt obfuscation patterns in real-time based on detection attempts.
Quantum-Safe Protocols
New encryption methods designed to withstand quantum computer attacks on current obfuscation techniques.
Frequently Asked Questions
Ready to Experience True Internet Freedom?
Join millions of users who trust Surfshark’s advanced obfuscation technology to bypass censorship and protect their privacy.
Get Surfshark VPN NowDisclosure: We may earn commission for purchases that are made by visitors on this site at no additional cost on your end. All information is for educational purposes and is not intended for financial advice. Read our affiliate disclosure.