Benefits of Using a VPN for Privacy and Security
Your Complete Guide to Online Protection
Table of Contents
Understanding VPN Privacy Benefits and Security
In today’s digital landscape, where cyber threats are escalating at an unprecedented rate, understanding VPN privacy benefits has become crucial for anyone seeking online protection. With over 1.5 billion VPN users worldwide and cyber attacks increasing by 30% in 2024 alone, the question “is VPN secure” has never been more relevant. This comprehensive guide explores how VPNs serve as powerful tools for anonymity, examining their effectiveness in protecting your digital footprint against sophisticated online threats.
Virtual Private Networks (VPNs) create encrypted tunnels between your device and the internet, masking your IP address and securing your data transmission. As cybercriminals employ increasingly sophisticated methods to exploit vulnerabilities, VPNs have emerged as essential shields against identity theft, data breaches, and invasive surveillance. This article will delve deep into the multifaceted benefits of VPN technology, backed by current statistics and expert analysis.
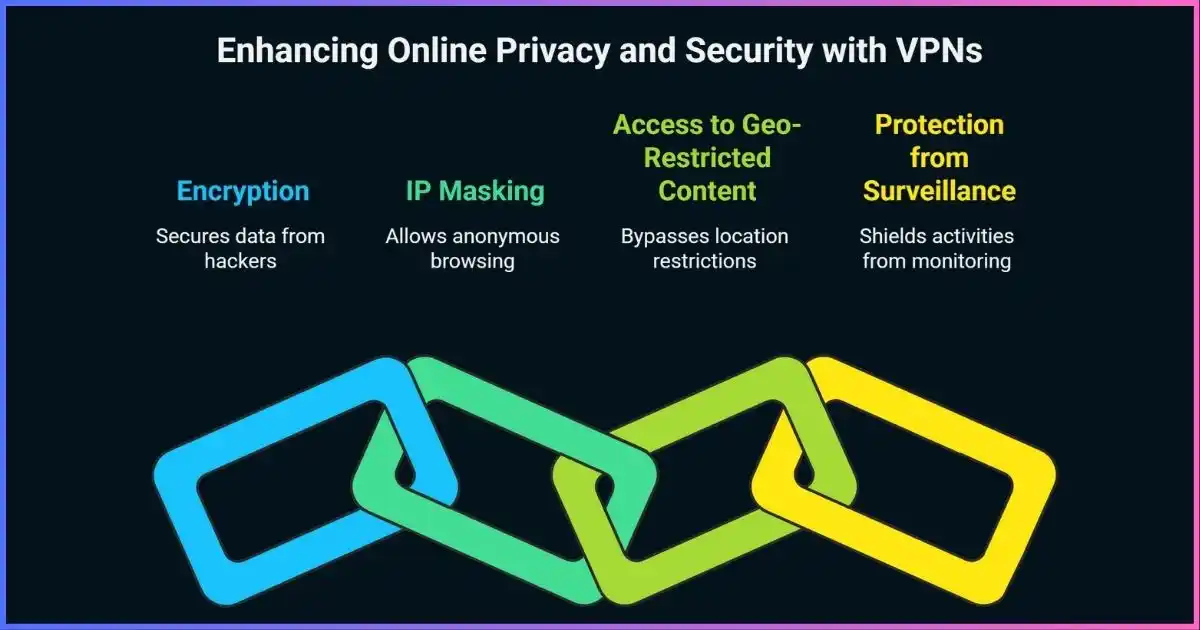
Key Takeaway: VPNs provide multi-layered protection through encryption, IP masking, and secure tunneling, making them indispensable tools for modern internet users concerned about privacy and security.
Core Privacy Benefits of VPNs
IP Address Masking and Location Privacy
One of the primary VPN privacy benefits is the ability to mask your real IP address, effectively hiding your geographical location and making it significantly harder for websites, advertisers, and malicious actors to track your online activities. When you connect to a VPN server, your internet traffic appears to originate from the server’s location rather than your actual position.
This IP masking capability provides several layers of protection. First, it prevents websites from building detailed profiles based on your location data. Second, it stops internet service providers from monitoring and logging your browsing habits. Third, it protects against geo-targeted attacks that exploit region-specific vulnerabilities.
Data Encryption and Traffic Protection
Modern VPNs employ military-grade encryption protocols, typically AES-256, to secure your data transmission. This level of encryption is virtually unbreakable with current technology, ensuring that even if your data is intercepted, it remains completely unreadable to unauthorized parties.
Encryption Strength Comparison
| Encryption Type | Key Length | Security Level | Time to Break |
|---|---|---|---|
| AES-128 | 128-bit | High | Billions of years |
| AES-256 | 256-bit | Military-grade | Longer than universe age |
| WEP | 64-128 bit | Weak | Minutes to hours |
ISP Monitoring Prevention
Internet Service Providers routinely monitor and log customer browsing activities, often selling this data to third parties or providing it to government agencies. VPNs create an encrypted tunnel that prevents ISPs from seeing your online activities, ensuring your browsing history remains private.
This protection is particularly important given recent legislative changes in various countries that have expanded ISP data collection and sharing capabilities. By encrypting your connection, VPNs ensure that your ISP can only see that you’re connected to a VPN server, not the specific websites or services you’re accessing.
Security Advantages: Is VPN Secure?
The question “is VPN secure” is fundamental to understanding their protective capabilities. The answer is definitively yes, when properly implemented and configured. VPNs provide multiple layers of security that work together to create a robust defense against various cyber threats.
Protection Against Public Wi-Fi Vulnerabilities
Public Wi-Fi networks represent one of the most significant security risks for internet users. These networks are often unsecured, allowing cybercriminals to easily intercept data transmitted over them. According to recent surveys, securing public Wi-Fi connections is the number one reason people use VPNs, with 52% of users citing this as their primary motivation.
VPNs eliminate these risks by encrypting all data before it leaves your device, ensuring that even if malicious actors intercept your traffic on public networks, they cannot decipher the encrypted information.
Defense Against Man-in-the-Middle Attacks
Man-in-the-middle (MITM) attacks occur when cybercriminals position themselves between your device and the websites you visit, intercepting and potentially modifying your communications. VPNs prevent these attacks by establishing secure, encrypted connections that cannot be compromised through traditional MITM techniques.
DNS Leak Protection
DNS leaks represent a significant vulnerability that can expose your browsing activities even when using a VPN. Quality VPN services implement DNS leak protection, ensuring that all DNS queries are routed through encrypted tunnels rather than through your ISP’s DNS servers.
VPN for Anonymity: Advanced Privacy Protection
Using a VPN for anonymity goes beyond basic privacy protection, offering sophisticated features that make it extremely difficult for any party to trace your online activities back to your real identity. This level of protection is particularly important for journalists, activists, and privacy-conscious individuals operating in restrictive environments.
No-Logs Policies and Jurisdiction Considerations
The effectiveness of VPNs for anonymity largely depends on the provider’s logging policies and legal jurisdiction. Reputable VPN services implement strict no-logs policies, meaning they don’t store any information about your online activities, connection times, or IP addresses.
Important Consideration:
VPN providers based in countries with strong privacy laws and outside the “Five Eyes” intelligence alliance generally offer better anonymity protection. These jurisdictions have limited data retention requirements and stronger legal protections against surveillance.
Advanced Anonymity Features
Modern VPN services offer several advanced features that enhance anonymity protection:
- Multi-hop connections: Route traffic through multiple VPN servers in different countries
- Tor over VPN: Combine VPN encryption with Tor network anonymity
- Obfuscated servers: Disguise VPN traffic to bypass deep packet inspection
- Kill switches: Automatically disconnect internet if VPN connection drops
- Split tunneling: Choose which applications use the VPN connection
Browser Fingerprinting Protection
While VPNs excel at hiding your IP address, they don’t inherently protect against browser fingerprinting techniques that can identify you based on your browser configuration, installed plugins, and system characteristics. However, when combined with privacy-focused browsers and proper configuration, VPNs significantly enhance overall anonymity.
Current Cyber Threat Landscape
Understanding the current cyber threat landscape is crucial for appreciating why VPN privacy benefits have become so essential. The year 2024 has witnessed an unprecedented escalation in cybercriminal activities, with sophisticated attack vectors targeting individuals and organizations worldwide.
Escalating Attack Frequency and Sophistication
Recent data reveals alarming trends in cybercrime activity. Global cyber attacks increased by 30% in Q2 2024, reaching an average of 1,636 weekly attacks per organization. This represents more than 2,200 cyberattacks occurring daily worldwide, demonstrating the persistent and evolving nature of digital threats.
The sophistication of these attacks has also increased dramatically. Cybercriminals now employ artificial intelligence and machine learning to enhance their attack methodologies, making traditional security measures less effective. This evolution underscores the importance of comprehensive protection strategies that include VPN usage.
Financial Impact of Data Breaches
The financial consequences of cyber attacks continue to escalate. The global average cost of a data breach reached an all-time high of $4.88 million in 2024, representing a 10% increase from the previous year. These costs encompass direct financial losses, regulatory fines, remediation expenses, and long-term reputational damage.
Critical Statistics:
- • 68% of data breaches involve human elements
- • Over 6.8 billion records were compromised in 2024
- • Phishing attacks increased by 202% in the second half of 2024
- • IoT malware attacks surged by 107%
Targeted Attack Vectors
Cybercriminals are increasingly targeting specific vulnerabilities that VPNs can effectively mitigate. Public Wi-Fi networks remain prime targets, with attackers deploying fake hotspots and packet sniffing tools to capture sensitive information. Additionally, ISP-level surveillance and data collection have become more prevalent, making encrypted VPN connections essential for maintaining privacy.
VPN Protocols and Encryption Standards
The security effectiveness of VPNs largely depends on the protocols and encryption standards they employ. Different protocols offer varying levels of security, speed, and compatibility, making it important to understand their characteristics when evaluating VPN services.
Modern VPN Protocols
Contemporary VPN services primarily utilize four main protocols, each with distinct advantages and use cases:
OpenVPN
Considered the gold standard for VPN security, OpenVPN offers exceptional flexibility and security. It uses AES-256 encryption and is highly configurable, making it suitable for various security requirements.
WireGuard
A newer protocol that combines high security with exceptional performance. WireGuard uses modern cryptographic techniques and offers faster connection speeds while maintaining strong security.
IKEv2/IPSec
Excellent for mobile devices due to its ability to quickly reconnect after network changes. Offers strong security and is particularly effective for users who frequently switch between networks.
L2TP/IPSec
Provides good security when properly configured but may be slower than other protocols. Widely supported across different platforms and devices.
Encryption Implementation
The effectiveness of VPN security depends not only on the protocol but also on the encryption implementation. Advanced Encryption Standard (AES) with 256-bit keys represents the current gold standard, providing security that would take longer than the age of the universe to break using current computational methods.
Additional security features like Perfect Forward Secrecy (PFS) ensure that even if encryption keys are compromised, past communications remain secure. This is achieved by generating new encryption keys for each session, preventing retroactive decryption of captured data.
VPN Usage Statistics and Market Trends
The VPN market has experienced explosive growth, driven by increasing awareness of privacy concerns and the escalating cyber threat landscape. Current statistics reveal significant adoption patterns and user motivations that underscore the importance of VPN technology.
Global Adoption Patterns
Approximately 1.5 billion people worldwide currently use VPN services, representing about 22.9% of global internet users. This adoption rate varies significantly by region, with some countries showing usage rates exceeding 55% of the population. The COVID-19 pandemic accelerated VPN adoption in the United States by 124%, highlighting the technology’s importance for remote work and secure communications.
Key Usage Statistics
User Motivations and Preferences
Research indicates that 52% of VPN users opt for paid services rather than free alternatives, recognizing the superior security and privacy protections offered by premium providers. The primary motivations for VPN usage include:
- Public Wi-Fi security (cited by majority of users)
- Prevention of ISP tracking and monitoring
- Protection against search engine and social media tracking
- Access to geo-restricted content
- Enhanced anonymity for sensitive communications
Interestingly, nearly 40% of users specifically rely on VPNs to prevent tracking from search engines and social media platforms, demonstrating growing awareness of digital privacy concerns and the pervasive nature of online surveillance.
Choosing the Right VPN Service
Selecting an appropriate VPN service is crucial for maximizing privacy benefits and security protection. With numerous providers in the market, understanding key evaluation criteria helps ensure you choose a service that meets your specific needs and provides genuine protection.
Essential Evaluation Criteria
When evaluating VPN services, several critical factors determine their effectiveness for privacy and security:
No-Logs Policy Verification
Look for providers with independently audited no-logs policies. Third-party audits provide credible verification that the service doesn’t store user activity data, connection logs, or identifying information.
Jurisdiction and Legal Framework
Consider providers based in privacy-friendly jurisdictions with strong legal protections against surveillance and data retention requirements. Countries outside the “Five Eyes” alliance typically offer better privacy protections.
Security Features and Protocols
Ensure the service offers modern protocols like OpenVPN or WireGuard, AES-256 encryption, DNS leak protection, and kill switch functionality. Advanced features like obfuscation and multi-hop connections provide additional security layers.
Performance and Reliability
Evaluate connection speeds, server network size, and uptime reliability. Quality providers typically reduce speeds by only 10-20% while maintaining stable connections across their server network.
Red Flags to Avoid
Certain characteristics indicate potentially unreliable or unsafe VPN services:
- Free services that claim “no limits” (often monetize user data)
- Lack of transparency about ownership and jurisdiction
- Absence of independent security audits
- Unclear or misleading privacy policies
- Extremely cheap pricing that seems unsustainable
- No kill switch or DNS leak protection
Recommended: ExpressVPN
Based on comprehensive evaluation criteria, ExpressVPN consistently ranks among the top VPN services for privacy and security. Key advantages include:
- Independently audited no-logs policy
- British Virgin Islands jurisdiction (privacy-friendly)
- AES-256 encryption with multiple protocol options
- Extensive server network across 94 countries
- 24/7 customer support and 30-day money-back guarantee
Frequently Asked Questions
How secure is a VPN really?
Modern VPNs using protocols like OpenVPN or WireGuard with AES-256 encryption are extremely secure. The encryption strength would take longer than the age of the universe to break using current computational methods. However, security depends on proper implementation, no-logs policies, and the provider’s trustworthiness.
Can VPNs provide complete anonymity online?
While VPNs significantly enhance anonymity by masking IP addresses and encrypting traffic, complete anonymity requires additional measures. Browser fingerprinting, cookies, and account-based tracking can still identify users. For maximum anonymity, combine VPNs with privacy-focused browsers, regular cookie clearing, and careful online behavior.
Do free VPNs provide adequate privacy protection?
Free VPNs often compromise user privacy to generate revenue. Research shows that 85% of top free VPNs still share user data despite privacy claims. Free services typically offer limited bandwidth, slower speeds, fewer servers, and may log user activities. Paid services generally provide superior privacy protection and security features.
Will using a VPN slow down my internet connection?
VPNs typically reduce connection speeds by 10-30% due to encryption overhead and routing through VPN servers. Quality providers minimize this impact through optimized server networks and efficient protocols. The security and privacy benefits usually outweigh the minor speed reduction for most users.
Are VPNs legal to use?
VPNs are legal in most countries and are commonly used by businesses and individuals for legitimate security purposes. However, some countries restrict or ban VPN usage. Additionally, using VPNs for illegal activities remains illegal regardless of the technology used. Always comply with local laws and terms of service.
How do I know if my VPN is working properly?
Test your VPN effectiveness by checking your IP address before and after connection, running DNS leak tests, and verifying that your traffic is encrypted. Many VPN providers offer built-in testing tools, and independent websites provide comprehensive leak testing services to ensure your privacy protection is functioning correctly.
Conclusion: The Essential Role of VPNs in Digital Privacy
The evidence overwhelmingly demonstrates that VPN privacy benefits are not just advantageous but essential in today’s digital landscape. With cyber attacks increasing by 30% in 2024 alone and data breaches costing an average of $4.88 million, the question is no longer whether VPNs are secure, but rather how quickly you can implement comprehensive privacy protection.
VPNs for anonymity represent a fundamental shift in how we approach online privacy, providing military-grade encryption that protects against sophisticated threats while preserving our digital freedom. As 1.5 billion users worldwide have already discovered, VPNs offer practical, effective solutions to real privacy challenges that affect everyone from casual internet users to security professionals.
The current threat landscape, characterized by escalating attack sophistication and frequency, makes VPN usage a critical component of personal cybersecurity strategy. The technology’s ability to provide IP masking, traffic encryption, ISP monitoring prevention, and protection against public Wi-Fi vulnerabilities creates multiple layers of defense that are increasingly difficult for malicious actors to penetrate.
Take Action Today
Don’t wait for a security incident to prioritize your online privacy. Start protecting your digital life with a trusted VPN service.
Start Your Privacy Protection Journey30-day money-back guarantee • No-logs policy • 24/7 support
Remember that choosing the right VPN service is crucial for maximizing these benefits. Look for providers with independently audited no-logs policies, strong encryption standards, reliable performance, and transparent privacy practices. The investment in quality VPN protection is minimal compared to the potential costs of privacy violations and security breaches.
As digital privacy concerns continue to evolve and cyber threats become more sophisticated, VPNs will remain essential tools for maintaining online security and anonymity. The time to implement comprehensive VPN protection is now, before you become another statistic in the growing list of privacy violations and security incidents.
Disclosure: We may earn commission for purchases that are made by visitors on this site at no additional cost on your end. All information is for educational purposes and is not intended for financial advice. Read our affiliate disclosure.