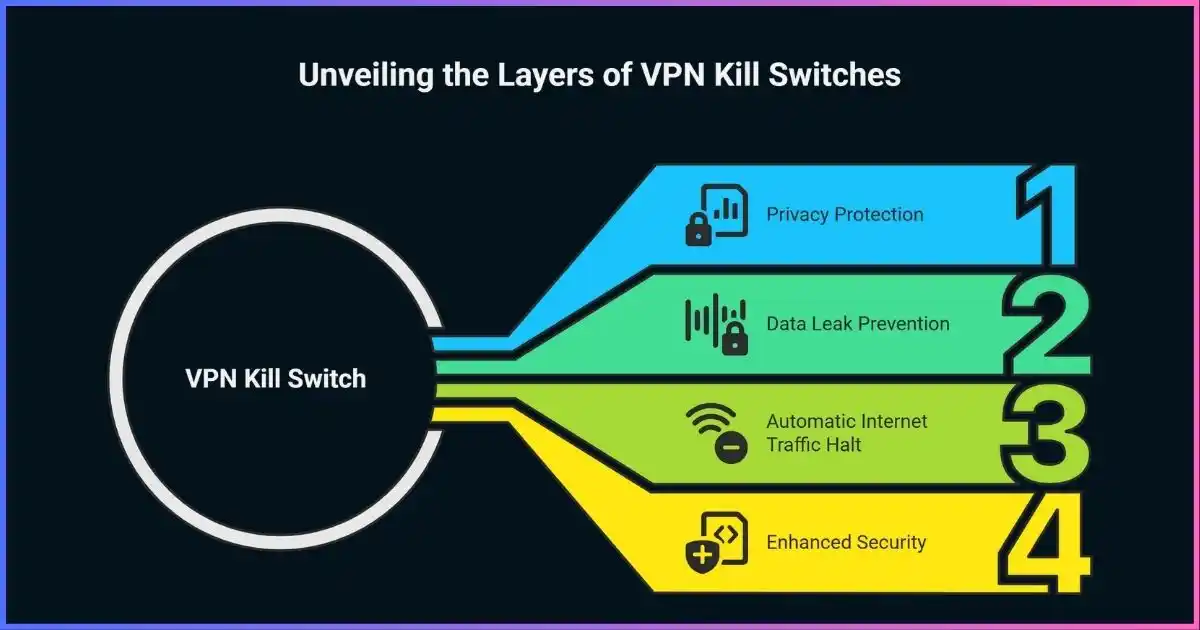
How Kill Switches Work in VPNs: Complete Guide to VPN Kill Switch Technology
Understanding VPN kill switches is crucial for maintaining online privacy and security. This comprehensive guide explains how these essential security features work, their types, benefits, and why they’re indispensable for protecting your data from potential leaks.
Table of Contents
What is a VPN Kill Switch?
A VPN kill switch is a critical security feature that automatically disconnects your device from the internet if your VPN connection drops unexpectedly. This safety mechanism ensures that your real IP address, location, and sensitive data remain protected even when the VPN tunnel fails.
Think of it as an emergency brake for your internet connection. When the VPN kill switch detects that the secure tunnel between your device and the VPN server has been compromised, it immediately blocks all internet traffic until the VPN connection is restored or manually disabled.
Key Point: Without a kill switch, your device might automatically reconnect to the internet using your regular connection, potentially exposing your real IP address and browsing activity to your ISP, government agencies, or malicious actors.
According to recent cybersecurity research, over 5.5 billion online accounts worldwide were breached in alone, making VPN kill switches more crucial than ever for protecting sensitive information during unexpected connection drops.
How VPN Kill Switches Work
VPN kill switches operate through continuous monitoring and automated response mechanisms. Here’s a detailed breakdown of the technical process:
Continuous Monitoring
The kill switch constantly monitors your VPN connection status, checking for:
- VPN server connectivity
- Tunnel integrity
- IP address changes
- DNS leak detection
Instant Response
When a connection drop is detected, the kill switch immediately:
- Blocks all internet traffic
- Prevents IP address exposure
- Maintains application isolation
- Logs the disconnection event
Technical Implementation
VPN kill switches work at different levels of your system architecture:
| Implementation Level | How It Works | Response Time |
|---|---|---|
| Network Interface | Monitors network adapter status and routing tables | Milliseconds |
| Application Layer | Watches specific application traffic patterns | 1-2 seconds |
| Firewall Rules | Implements immediate traffic blocking policies | Instant |
Types of VPN Kill Switches
VPN kill switches come in two primary types, each offering different levels of protection and control. Understanding these differences is crucial for choosing the right VPN service for your security needs.
System-Level Kill Switch
A system-level kill switch monitors your entire internet connection and blocks all network traffic when the VPN disconnects.
Advantages:
- Complete system protection
- No application-specific configuration needed
- Protects all internet-connected apps
- Maximum security coverage
Disadvantages:
- Can interrupt all internet activities
- May cause frequent disconnections on unstable connections
- Less granular control
Application-Level Kill Switch
An application-level kill switch allows you to select specific applications that will be disconnected when the VPN fails.
Advantages:
- Selective application protection
- Continued internet access for other apps
- Better user experience
- Flexible configuration options
Disadvantages:
- Requires manual configuration
- May miss newly installed applications
- Less comprehensive protection
Expert Recommendation: For maximum security, choose a VPN provider like NordVPN that offers both system-level and application-level kill switches, allowing you to customize protection based on your specific needs.
VPN Kill Switch Statistics and Market Data
Recent research reveals compelling statistics about VPN usage and the importance of kill switch technology in cybersecurity:
46%
of Americans now use VPNs (up from 39% in )
95%
of adults are familiar with VPN technology
5.5B
online accounts breached in
VPN Usage Reasons ()
Global VPN Adoption by Region
VPN Kill Switch Implementation Comparison
| Feature | System-Level | Application-Level |
|---|---|---|
| Security Level | Maximum | Selective |
| User Experience | May interrupt workflows | Seamless for unprotected apps |
| Configuration | Automatic | Manual setup required |
| Response Time | Immediate | Near-immediate |
| Best For | High-security environments | Balanced security/usability |
Related: Split Tunneling vs Full Tunneling
Related: DNS Leaks and How to Prevent Them
Benefits of VPN Kill Switches
VPN kill switches provide essential protection against various cybersecurity threats. Here are the key benefits that make them indispensable for online privacy:
Prevents Data Leaks
Kill switches ensure that your real IP address and browsing data never leak to your ISP, government agencies, or malicious actors when VPN connections drop unexpectedly.
Maintains Anonymity
By blocking all traffic during VPN disconnections, kill switches preserve your online anonymity and prevent location tracking across all your internet activities.
Public Wi-Fi Protection
On public networks, kill switches provide critical protection against man-in-the-middle attacks and prevent accidental connections to unsecured networks.
ISP Tracking Prevention
Kill switches prevent your ISP from logging your browsing history, downloading activities, and online behavior patterns during VPN connection failures.
Real-World Protection Scenarios
Scenario 1: Unstable Internet Connection
During a video call or file transfer, your internet connection becomes unstable. Without a kill switch, your device might reconnect using your real IP, exposing your location and activities to third parties.
Scenario 2: VPN Server Maintenance
When VPN servers undergo maintenance or experience overload, connections can drop suddenly. A kill switch ensures your torrenting activities or sensitive communications remain private.
Scenario 3: Network Switching
When your device switches between Wi-Fi and mobile data, brief disconnections can occur. Kill switches prevent any unprotected data transmission during these transitions.
Choosing a VPN with Kill Switch
When selecting a VPN service, the quality and reliability of the kill switch feature should be a top priority. Here’s what to look for:
Essential Features to Look For
- Always-on Kill Switch: Automatic activation on all connections
- Multi-platform Support: Available on Windows, Mac, iOS, and Android
- Customizable Settings: Both system-level and application-level options
- No Logging Policy: Zero-log guarantee for maximum privacy
- DNS Leak Protection: Prevents DNS query exposure
Additional Security Features
- Split Tunneling: Selective VPN routing for specific applications
- Double VPN: Extra encryption layer through multiple servers
- Threat Protection: Built-in malware and ad blocking
- Obfuscated Servers: Bypass VPN detection and censorship
- 24/7 Support: Technical assistance when needed
Why NordVPN Stands Out
NordVPN offers one of the most comprehensive kill switch implementations in the industry:
- System-level and app-level kill switches
- Always-on protection by default
- 6,000+ servers worldwide
- 30-day money-back guarantee
Frequently Asked Questions
When a VPN kill switch activates, it immediately blocks all internet traffic from your device. This prevents your real IP address from being exposed and stops any data from being transmitted outside the secure VPN tunnel. The kill switch remains active until the VPN connection is restored or you manually disable it.
No, not all VPNs include kill switches. Many free VPNs and some budget providers don’t offer this feature. It’s crucial to verify that your chosen VPN provider includes a reliable kill switch, especially if you handle sensitive data or engage in activities requiring maximum privacy protection.
Yes, most VPN providers allow you to disable the kill switch feature through their application settings. However, this is generally not recommended as it leaves you vulnerable to data leaks during connection drops. Some providers like NordVPN have the kill switch enabled by default for maximum security.
A properly implemented kill switch should not significantly impact your internet speed during normal operation. The monitoring process runs in the background with minimal resource usage. Speed impacts typically only occur during the brief moments when the kill switch is actively blocking traffic due to VPN disconnections.
You can test your kill switch by deliberately disconnecting from your VPN server while monitoring your IP address. If the kill switch is working correctly, your internet connection should be blocked, and you shouldn’t be able to access websites or check your IP address until the VPN reconnects.
Mobile kill switches can be just as effective as desktop versions, but they face unique challenges due to mobile operating system restrictions. iOS and Android handle VPN connections differently, and some mobile kill switches may not work when the VPN app is closed or during system restarts. Look for VPN providers that offer always-on VPN options for mobile devices.
Protect Your Privacy with Advanced Kill Switch Technology
Don’t leave your online security to chance. Choose a VPN with reliable kill switch protection and enjoy complete peace of mind.
Get NordVPN with Kill Switch ProtectionDisclosure: We may earn commission for purchases that are made by visitors on this site at no additional cost on your end. All information is for educational purposes and is not intended for financial advice. Read our affiliate disclosure.